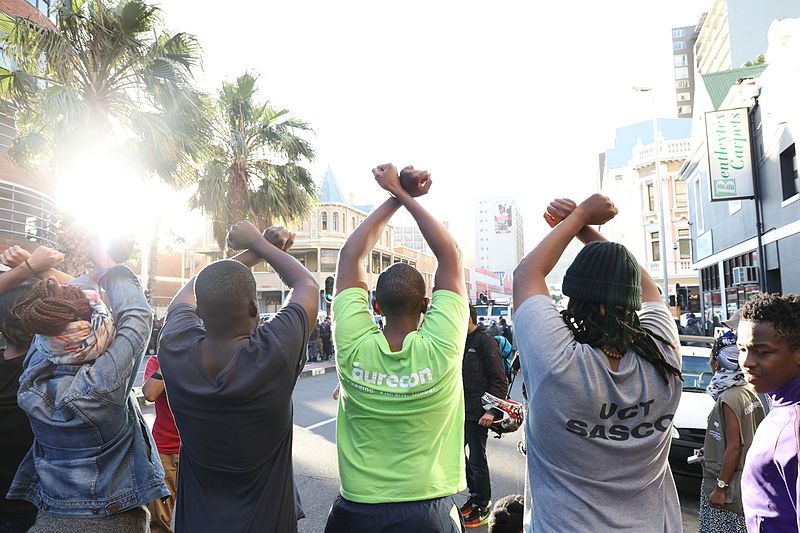During December 2018 and January 2019, there were two online protests against the governments of Sudan and Zimbabwe. In both protests, the hacktivism group, Anonymous, used what is known as a Distributed Denial-of-Service (DDoS) attack to disable government-related websites in both Afrikan countries.
Speaking to iAfrikan.com, one of the people involved in carrying out the DDoS attacks for Anonymous, Lorian Syriano, explained that they used DDoS as a form of protest.
"The DDoS attacks aim to shut down the targeted website or server as a form of protest."
Given the attention the attacks received from across the continent and the world, it seems there is a misunderstanding of what a DDoS attack is and whether it is permanent or not. This article aims to clarify that.
What is a protest?
A protest, simply put, can be broken down into two parts:
- Disagreeing with something.
- Bringing attention to the grievance/disagreement.
Using the #FeesMustFall student protests that took place in South Africa, they displayed both simplified characteristics of our definition of a protest. Firstly, the students disagreed with South Africa's government and universities that they should be required to pay for education. Secondly, through mass protests, they brought attention to their grievance.
This is no different from what DDoS achieves via the Internet when used as a form of protest.
DDoS explained
Simply put, a DDoS attack is an attempt to disrupt normal traffic of a targeted server, service, or network, by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. This is in a similar way that a mass protest in real-life would disrupt access to key roads and buildings in order to disrupt their operations and bring attention to a specific grievance.
DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems (bots) as their sources of generating Internet traffic to attack targeted systems. These compromised compromised computer systems can include computers and other networked resources such as IoT devices.
To use another analogy, a DDoS attack is like a traffic jam clogging up the highway, preventing regular traffic from arriving at its desired destination, as Cloudflare puts it.
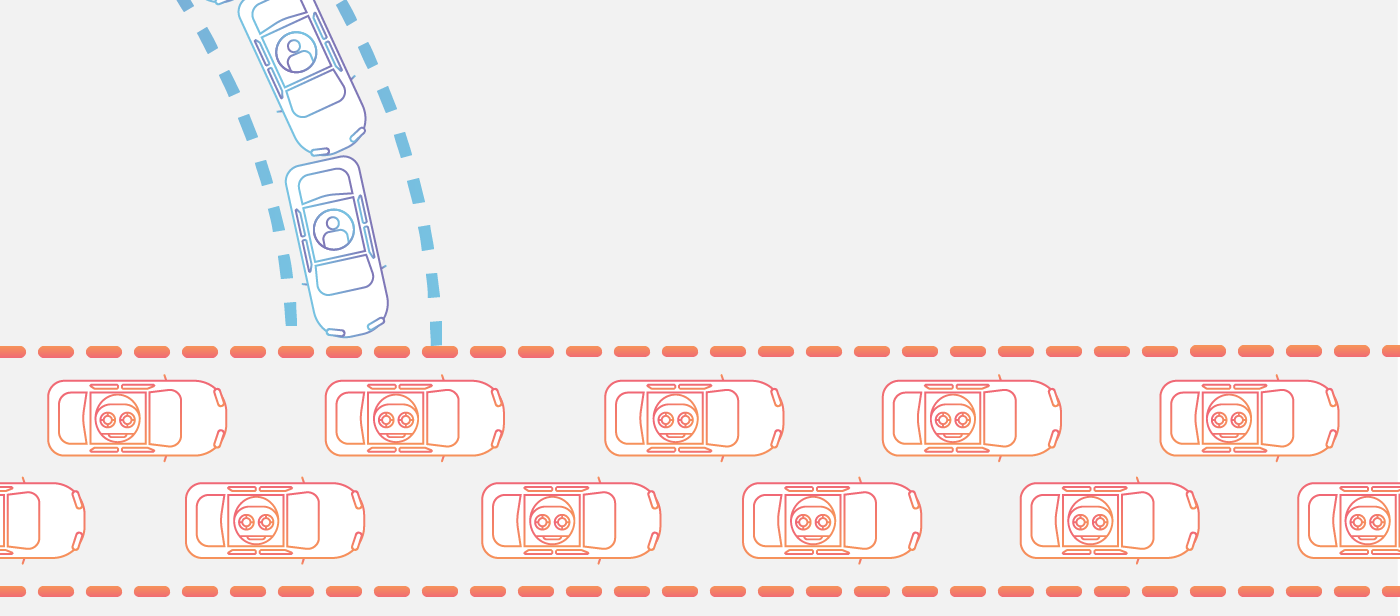
It is understandable that DDoS is mainly frowned upon by some ICT professionals as it has, in many cases, been used for more malicious purposes than just as a form of protest. However, as Anonymous and other protest groups have illustrated, it can be a useful, albeit a temporary, form of online protest too.
— By Tefo Mohapi