By Tefo Mohapi
One of Nigeria's more popular online sports betting companies, SureBet247 (surebet247[.]com), has suffered a potential security and data breach which put thousands of their customers and their systems at risk. The data was found by an anonymous source who tipped off Australian security researcher and Founder of haveibeenpwned, Troy Hunt. Hunt subsequently got in touch with me after several days of failed attempts to reach SureBet247 and alert them that their customers and business could be at risk had failed.
SureBet247 is owned by Chessplus International Ltd, a Nigerian company that specializes in online gambling and casinos co-founded by Sherif Olaniyan and Olasupo Badmus when they apparently met at University in Ilorin in Nigeria.
"The data was sent to me by an anonymous party who wanted the incident to come to light. They’d tried to make contact with Surebet247 but stated it was without success. The data is extensive spanning over 32GB of backups across 6 databases of various online betting assets. Within the databases there’s everything from user records to betting histories, the latter consuming more than 100M rows in one of the databases," said Hunt.
We were able to verify that the database, which includes data and table names such as the following (and many more) belongs to SureBet247 given the list of staff e-mail addresses, some data linked to the surebet247[.]com domain and more:
Table Name No. of records
BetSlipFolds 18540474
BetSlipLogs 102955033
EvaluateAuthorizeBetSlipsDT 12362
SourceCompetitors 92059
Transactions 966045
UserProfiles 377657
Users 377681Frustration with SureBet247 support
As Hunt put it, 8 days ago his anonymous contact had tried, with no success, to alert the SureBet247 support team of the potential breach and risk, they received no response. Three days later after that, Hunt also tried to contact the Nigerian betting operator's support team and got no response.
It was only on Tuesday 31 December 2019, after iAfrikan.com tried various methods of getting hold of the people at SureBet247, that eventually there was a response. However, the frustration continued as the company continued to display a nonchalant attitude to the potential security and data breach they could have suffered.
When I alerted one of the Nigerian betting operator's customer care agents that we need a person that we can get in touch with and explain the breach and the data that was able to be accessed and possibly see how they can secure their systems, the agent answered, without asking for any further information, "We have done that sir. Thank you."
Realizing that perhaps the agent doesn't understand the urgency of my communication, I asked if there's a technical support person I can get in touch with at SureBet247, I was referred to the same e-mail address that Hunt had e-mailed before. Just like him, I received no answer from their technical support.
At this point, a day later, I contacted the customer care agent again trying to explain how serious this is and at minimum, they need to alert their customers of the potential breach and the risks they face should their data fall into the wrong hands. Furthermore, I explained to the agent that it is better if they alerted their customers rather than they hear of the data breach via media publications, the agent responded by saying:
"That is ours to decide."
At this point, it became clear that, given our experience with Nigeria's SureBet247, they were unlikely to notify their customers and were not taking the breach seriously. Further highlighting the problem that many companies don't take data and security breaches seriously. Not only that, one would expect that a company that handles financial transactions would treat a potential security breach alert with urgency and have processes in place on how to deal with such potential breaches once they have been communicated to them.
More betting companies affected?
Initially, we thought the database only related to Nigeria's SureBet247 and some of their related online assets, but upon closer inspection, it appeared that other online sports betting operators could be affected given the names of the databases that were shared with us.
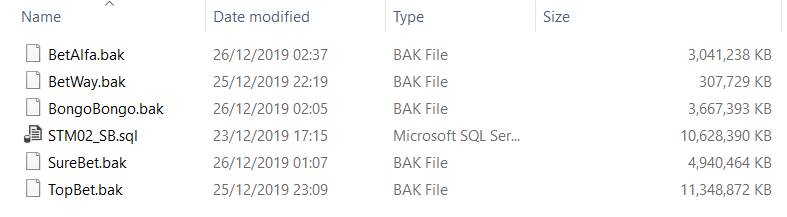
Apart from the databases, the anonymous source also mentioned that they "have the source code of the following sites,"
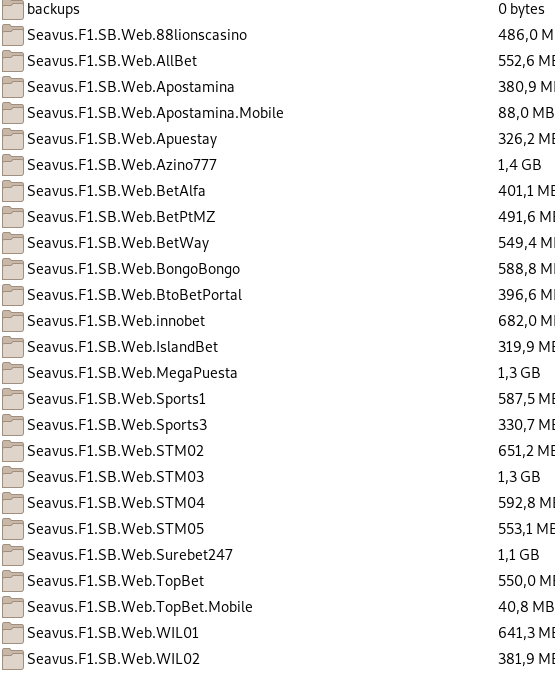
Looking at the directory, some of the companies whose databases they shared also appear in this list (including SureBet247) of source code. However, one name caught my attention which I initially thought was just a randomly named server name - Seavus.
A quick Google search revealed that Seavus might not just be a randomly named server but a name of a Swedish software development company that coincidentally develops and sells "iGaming Solutions" to provide what they call "endless possibilities for iGaming and betting operators."
At this stage, it was not clear whether we are looking at a compromise and breach of Seavus' software, a breach of a few (or one) betting operators who run what Seavus call a "multi-brand platform", or if this indeed is a data and security breach at each of the betting operators.
"I’m yet to total the user records, but multiple databases contained hundreds of thousands of user records each so the number is substantial. Impacted data includes names, email addresses, dates of birth, and betting records. It’s not yet clear whether passwords were also compromised, that’s something I’m hoping to clarify with them," added Hunt on the severity of the data breach on SureBet247.
NITDA investigates SureBet247
Nigeria's National Information Technology Development Agency (NITDA), the government organization responsible for implementing the country's National Information Technology Policy as well as overseeing enforcement of its Data Protection Regulations, has confirmed to iAfrikan.com that the Director-General, and CEO of NITDA, Mr. Kashifu Inuwa Abdullahi, gave an order for the incident to be investigated by NITDA's Data Breach Investigation Team.
"We are also sending a letter to the affected company to provide further details before we make our conclusions. NITDA appreciates the efforts of people like you who genuinely seek to reduce the flagrant breach of personal data globally," reads part of the message the NITDA sent to iAfrikan.com.
According to the NDPR, a company (among many other things) would be required to have a "Data Protection Officer" who would be responsible for communicating with "Data Subjects" and handling any issues relating to data protection. Thus far, it appeared that SureBet247 did not have such a role active.
After experiencing frustration with the Nigerian betting company's customer support agents, the company's co-founder and Managing Director, Sheriff Olaniyan, sent the following message to iAfrikan.com:
"Hi iAfrikan , The management of surebet247 seriously frown at this malicious news been promoted by your organization. We will not hesitate to take legal action if you don’t stop and bring this down. No customer data of ours was hacked or exposed ,you have many betting company names listed on the so called list why this personal attack on surebet247. It’s obvious there is a motive around this , you post fake news without disclaimer and your informant do not provide you customer list from any of the betting company claimed to be hacked. Names posted on your list told us how your informant was asking for payment and this was demanded from us , this is pure blackmail and you reported this news so personal without evidence. We will appreciate you stopped right now."
That communication would be the first and last time we heard from SureBet247 despite their legal threats.
At this stage, it is probably important to explain why we focussed on SureBet247 even though the data dump contained information (which we would only later piece together) from betting operators and software development companies. It's simple, the initial contact from the anonymous source mentioned, in the e-mail subject "Dumps surebet247.com and more." Looking into the data at a glance, it also becomes apparent why Surebet247 was the main focus - SureBet247 constituted the bulk of the data and code dump.
NAME OF DB NO. UNIQUE E-MAIL
STM02_SB.sql 2,166
BetAlfa 43,459
BetWay 78
BongoBongo 211,734
SureBet 410,384
TopBet 106,275As you can see, not only by the size of the data but by the number of both unique e-mail addresses (and user profiles, as detailed in the initial article), the SureBet247 data dump is by far the largest.
As attempts continued to engage with SureBet247 to try and not only get them to alert their users but also to try and help them identify the source of the breach so appropriate procedures and actions can be taken, it became apparent that the breach is possibly bigger in scope. This was also confirmed by the anonymous source who stated that (among other things that I cannot yet discuss as this is still a sensitive investigation and all the relevant parties need to be allowed sufficient time to respond) the security breach and data access was as a result of a security "vulnerability in a system and from there, escalate privileges."
This goes against what the company tweeted on 4 January 2020 stating that customer data was not accessed. Furthermore, what the company is saying is not true because, if that was the case, how come we could randomly verify that some of the user e-mails in the dump do exist as their betting portal users?
Given that the scale of the breach could stretch beyond Nigeria, it also brings another part of the West Afrikan country's NDPR possibly into play. Specifically, the parts relating to "Data Security", "Third Party Data Processing Contract" and the "Transfer (of data) to a foreign country." Should it become apparent that these two parts of NDPR were also violated, over and above the actual access of customer data, SureBet247 could stand to be possibly heavily punished by the NITDA.
The Data Security section of the NDPR specifically states that:
"Anyone involved in data processing or the control of data shall develop security measures to protect data; such measures include but not limited to protecting systems from hackers, setting up firewalls, storing data securely with access to specific authorized individuals, employing data encryption technologies, developing organizational policy for handling Personal Data (and other sensitive or confidential data), protection of emailing systems and continuous capacity building for staff."
Rise of online sports betting in Afrika
The SureBet247 potential security and data breach along with the potential data breach of other betting companies across Africa are also important in the context of the rise of online sports betting across Afrika, especially among the continent's youth. I cannot comment much on the socio-economic impact of online sports betting in Africa, however, some have reported that in some cases, mobile money loans are used for online sports betting, creating a vicious cycle.
What I do know though is that the trend of sports betting is growing across the continent if Google searches are anything to go by. If you look for example, at the top countries from where the phrase "sports betting" was searched from, 8 out of 10 of the top 10 are African countries as per Google Trends.
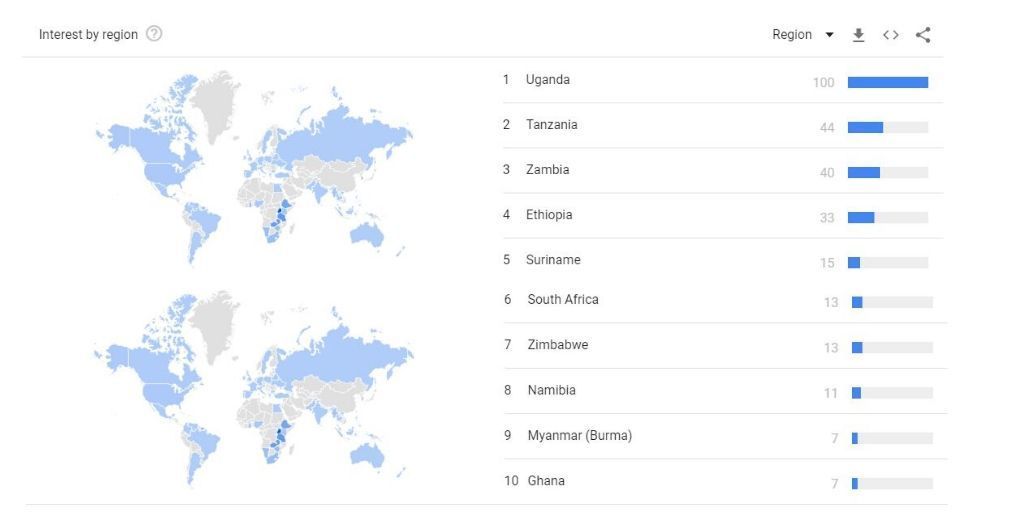
This sudden popularity has been explained in some quarters as a reflection of the desperation of Afrikans in dire need to make a living and make ends meet. It could also explain why during 2018 and 2019 there was a surge in new betting operators in Afrika as well as European companies such as BtoBet that announced many partnerships with betting operators across the continent.
BtoBet investigates security breach
BtoBet's betting customers in Afrika and South America were affected.
Further investigation and research revealed that BtoBet, the Macedonia-based company with headquarters in Gibraltar that sells online betting and casino software, suffered a security breach which resulted in the databases and code of its betting operator customers in Afrika and South America being accessed by a non-authorized person or people. This has been partly confirmed by BtoBet who, through their legal representative - Aleksandar Mihajloski who is a Partner and Attorney at Macedonia's Mihajloski & Popovska Law - told iAfrikan.com that the security breach is "subject to an ongoing criminal investigation."
BtoBet is a developer of sports betting and online casino technology solutions. These include not only customer-facing solutions that facilitate the user betting experience but also back-office technology solutions for betting operators such as analytics and a "White Label Partnership" solution that can be personalized and re-branded by any betting operator who uses it.
"I make reference to my email dated the 6th of January, 2020. As explained in that email, my client has immediately acted and notified the respective law enforcement and regulatory authorities, whilst also notifying hid direct customer. The situation you make reference to is subject to an ongoing criminal investigation. We have passed all the information related to this case to all the authorities involved," wrote Mihajloski when iAfrikan.com asked him about the security breach at BtoBet and whether the company was aware of it and had informed its betting operator customers.
Possible security vulnerability?
Initially, it was not obvious that BtoBet could be the source of the security and data breach that saw iAfrikan publish the article detailing how SureBet247 had suffered a data breach. As previously explained, the anonymous source who initially contacted Hunt, stated that they had "Dumps surebet247.com and more." Thus, this led to the initial investigation and research focussing on SureBet247.
However, as time passed and we inspected the data dump further, some clues started emerging. The first clue was how some of the betting websites whose names appeared in the data looked the same.
Further inspection and looking at the source code of each of the betting operators whose customer databases were part of the data dump revealed the first clue that BtoBet could be the company whose systems who breached and customer databases and code accessed.
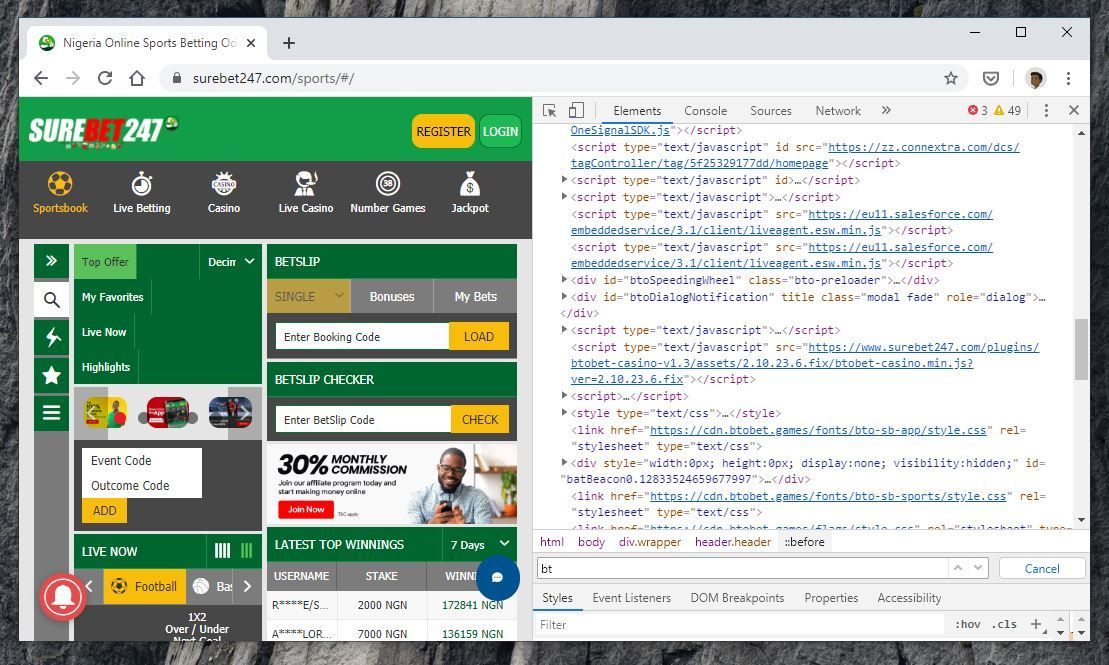
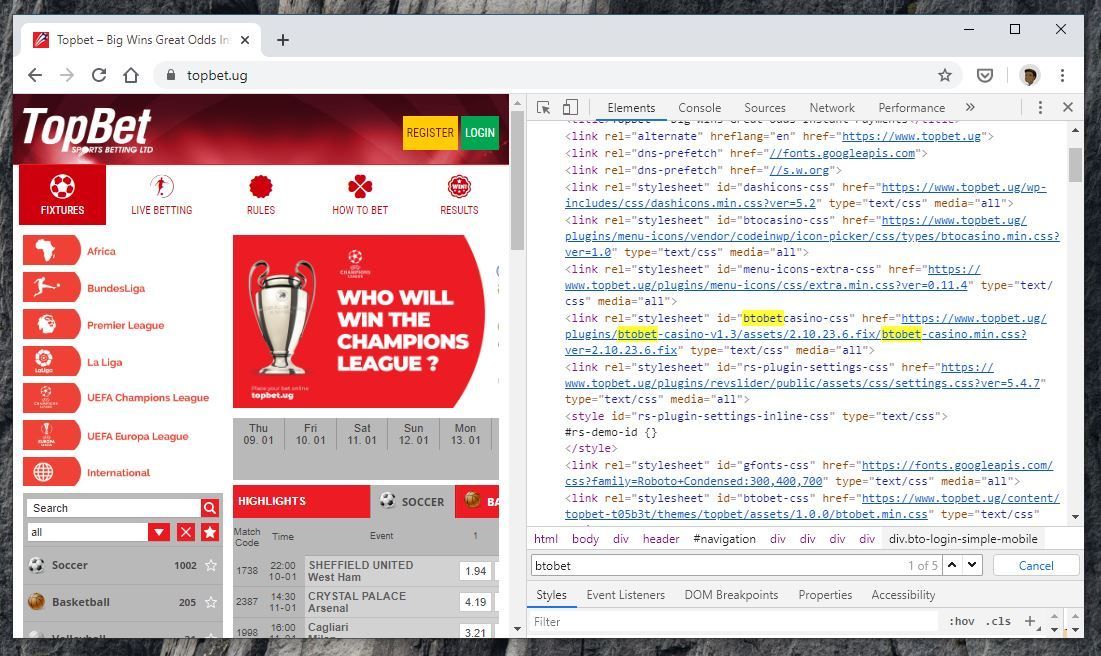
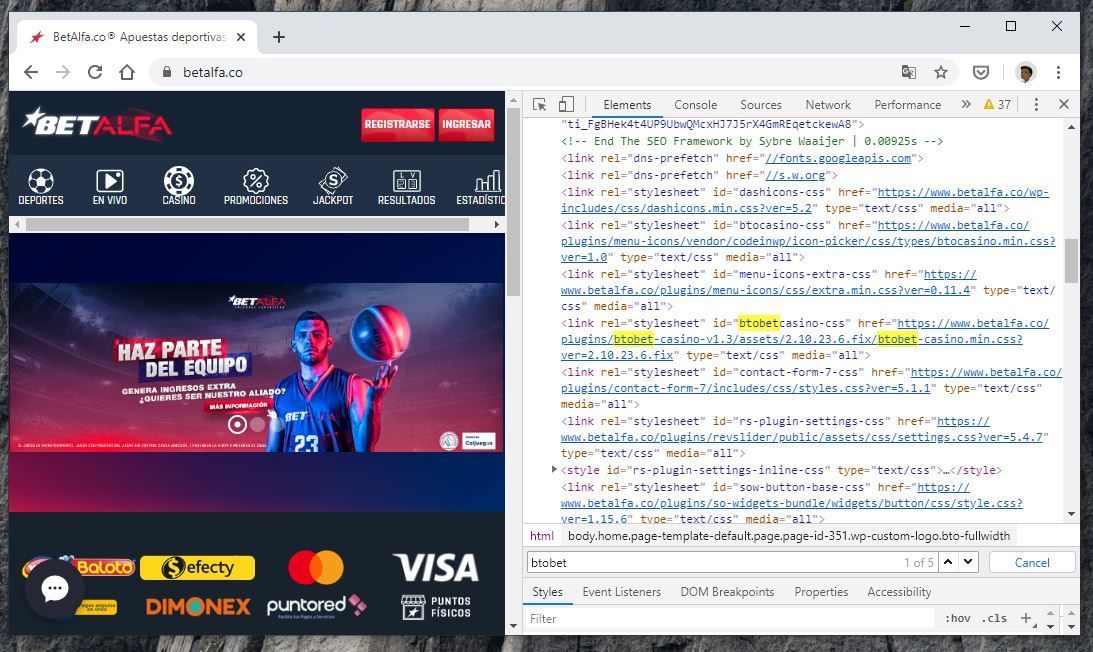
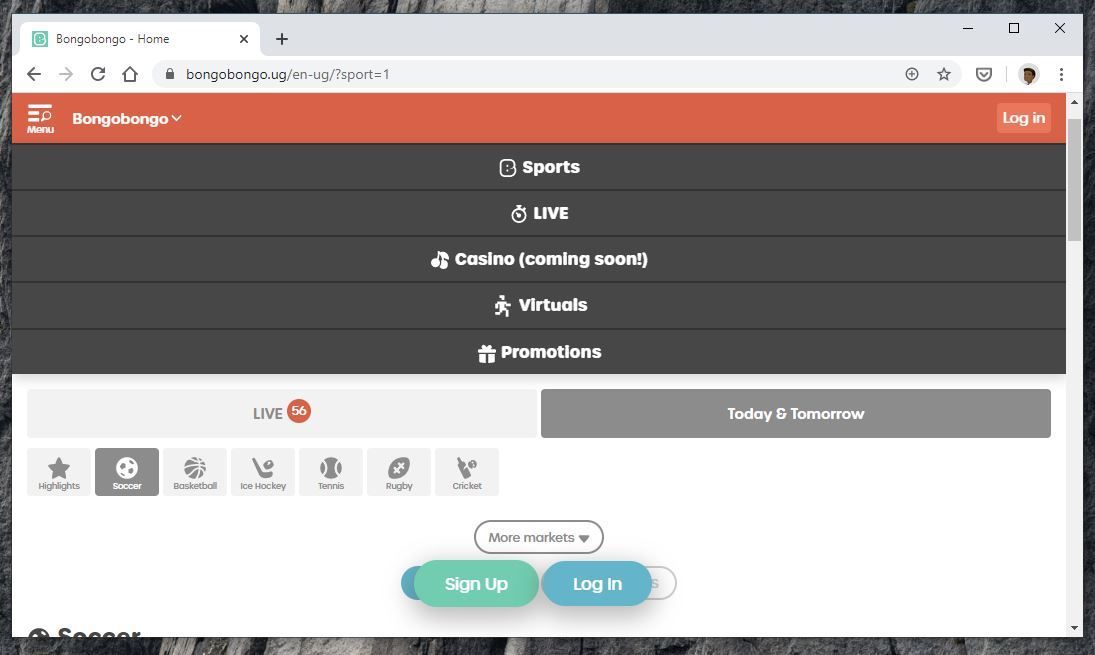
Another peculiar part of the data dump is a 307KB database backup filed named "BetWay.bak", although the file only contains 78 unique e-mail addresses, it is not clear why it was on BtoBet servers. This is made even more curious as when contacted by iAfrikan, BetWay wrote that "We have confirmed with Management and wish to reiterate that Betway in Nigeria does not operate on the BtoBet platform." This also seems to apply to all the countries they operate in across the continent.
However, I digress. With suspicions raised by the first couple of clues that we could be looking at a far reaching security possibly affecting many betting operators that use BtoBet software, we re-inspected the data dumps.
Before long, another clue that seemed to prove the working hypothesis that it was BtoBet's systems that were breached, Hunt discovered that each of the betting operators databases mentioned above which were part of the data dump had a lot of @btobet.com admin e-mail addresses (same e-mail address) at the beginning of each "Users" table.
After that, came another clue that almost conclusively proved that BtoBet had something to do with the security and data breach.
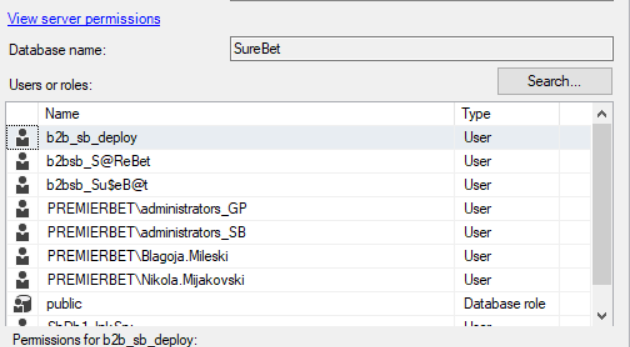
initially when looking at the permissions of all the databases that formed part of the data dump, it wasn't clear that BtoBet was being referenced in any way until we started searching for the two names that appear on them via Google. That's when it became almost clear that BtoBet was highly probably breached because Nikola Mijakovski's LinkedIn profile lists them as a "Principal Software Developer at BtoBet" while Blagoja Mileski's LinkedIn profile lists them as a "Technical Lead at BtoBet." Having tried to contact BtoBet and the Chief Marketing Officer previously without any success, I tried Nikola and Blagoja. No response after 24hrs. It was only when I contacted Bojan Gjorgjioski (Dotnet Developer at BtoBet) did I get an almost immediate response, although a rather strange one as Bojan, without asking any questions or making any remarks referred me to BtoBet's legal representative.
Initially, BtoBet was not forthcoming regarding the breach with Mihajloski sending a confusing message but would somehow later confirm the breach as mentioned at the beginning of this article.
"Respected, I am contacting you OBO my client BTOBET, regarding the information you have requested via email from members within the organization. Kindly be informed that we have notified the respective law enforcement officials and all the legal measures determined by the law are undertaken from their side. Whilst no serious digital breach has occurred, we have already taken all the necessary measures against unauthorized access by any malicious third party."
Further investigations
It is not clear what is to happen next and whether other customers of BtoBet are affected as well because the anonymous source said that they were able to access BtoBet's systems and "escalate permissions." At the time of publishing BetAlfa, BongoBongo, and TopBet Uganda had not responded to any communications from iAfrikan.com.
While SureBet247 is under investigation by Nigeria's Nigeria's National Information Technology Development Agency (NITDA), Mihajloski told iAfrikan.com that the alleged BtoBet security breach is under investigation by the Ministry of Interior of RN Macedonia - Sector for cybercrime and digital forensics.